This month, our new high level Cyber Security provided by Huntress detected a log in for one of our local clients from Kenya with multiple attempts made to login. Immediately the login was disabled and the hacker was stopped in their tracks.
Here we share snippets from a real life example of the report that we receive on a monthly basis that provide us with an overview of the security work that goes on behind the scenes. This gives you an insight in to the in depth analysis and monitoring that goes on continuously.
You can read our recent article about the change to Huntress Cyber Security here.
Overall Security Summary
During just one month, our cybersecurity platform analyzed 397,588 changes to the computer systems on our network in order to detect malicious activity.
Cyber Threat Hunters reviewed 331 potential threat indicators that were previously unknown or suspicious. In-depth investigations were conducted as needed and 2 cyber incident reports were created and responded to by our security team. This defense strategy continues to reduce our clients cyberattack risk, maximize security, and minimize downtime and damage to your businesses
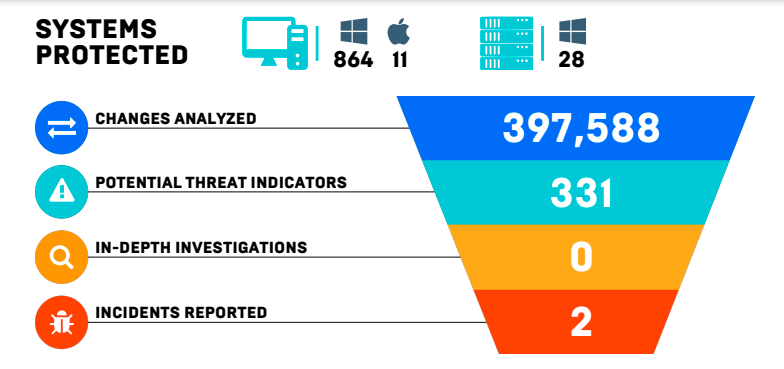
Looking at this, you can see that 331 potential threats were identified and two incidents were reported This means that the system is automatically flagging anything that looks even slightly out of the ordinary.
What is a persistent foothold?
Whilst this may sound more like something you should see the podiatrist about, Persistent Footholds are mechanisms attackers use to gain long-term access to a network by exploiting common auto-starting applications (autoruns), such as Skype or Google Updater.
By abusing and masquerading as legitimate system components, attackers can slip by other security tools, remaining undetected while planning their next move!!! Scary stuff.
During this month alone, our cybersecurity platform analyzed 397,588 changes to your systems in order to uncover persistent footholds that, if not remediated quickly, become malicious threats to your business. Cyber Threat Hunters (who are real people) manually reviewed 84 autoruns that were previously unknown or suspicious. As a result, our security team identified no persistent footholds on your computer systems. Phew!
Ransomware Canaries
Like the old canary in the coal mine, Ransomware Canaries enable faster and earlier detection of potential ransomware incidents. When deployed, small lightweight files are placed on all protected endpoints—and if those files are modified or changed in any way, an investigation is conducted.
What is Managed Antivirus?
Managed antivirus helps your security team proactively scan and enforce policy settings on your organization’s devices ensuring they are protected against the latest cyber threats. By aggregating antivirus findings into a single-pane of glass, your security team uses MAV to filter out noise and focus on the threats that are not mitigated by Antivirus alone.
During this timeframe, your Managed Antivirus (MAV) Service identified 42 suspicious detections, and automatically blocked 79 pieces of malware or potentially unwanted programs on Windows endpoints. Of the detections, 42 were auto-remediated by MAV and 0 required investigations by the team of cyber threat hunters.
What is MDR for Microsoft 365?
As a widespread and integral productivity suite, Microsoft 365 is a high profile target. MDR for Microsoft 365 monitors for suspicious and malicious behaviors that indicate compromise.
When a potential threat actor is detected in a Microsoft 365 service, a human reviews the activity, a remediation plan is established, and an alert is delivered through your Managed Security Platform.
During this report’s timeframe, MDR for Microsoft 365 analyzed the output of 189,010 events from your Microsoft 365 users and environment. The analysis revealed 4 events detected as potential threats that were manually reviewed by Cyber Threat Hunters. The review resulted in 4 in-depth investigations by our Cyber Threat Hunters. As a result, your security team identified and reported 3 malicious events among our tenants and took the necessary steps to secure our tenants.
In Summary
A cyber incident that is identified and remediated in a timely manner can save your company thousands if not millions of dollars depending on the size of your organization and the value of your data.
The best thing about all of this, is that you don’t need to do anything. Just sit back and know that we are taking care of everything in the background. Whilst no Cyber Security system is foolproof, this gives you an idea of how much monitoring is taking place on a 24/7 basis.
To discuss your individual requirements or to find out about the advantages of being on a Managed Service Plan and receiving this level of monitoring contact us here.



